 |
| |
| |
| |
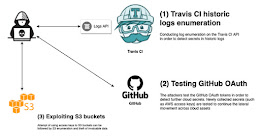 | Unpatched Travis CI API Bug Exposes Thousands of Secret User Access Tokens An unpatched security issue in the Travis CI API has left tens of thousands of developers' user tokens exposed to potential attacks, effectively allowing threat actors to breach cloud infrastructures, make unauthorized code changes, and initiate supply chain attacks. "More than 770 million logs of ... | |
 | Free eBook: Understanding Databases Deploy High-Performance Database Clusters in Modern Applications. Develop a high-level understanding of industry-standard databases, the design of database architectures, and different deployment methods in the cloud. Download instantly -- no registration required. Download ... | |
| |
| |
| |
| |
| |
| This email was sent to myemailku.ghdbrevo2018@blogger.com. You are receiving this newsletter because you opted-in to receive relevant communications from The Hacker News. To manage your email newsletter preferences, please click here.
 Contact The Hacker News: info@thehackernews.com Contact The Hacker News: info@thehackernews.com
Unsubscribe
The Hacker News | Pearls Omaxe, Netaji Subash Place, Pitampura, Delhi 110034 India |
0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home