 |
| |
| |
| |
| |
| |
 | Cloud-based Cryptocurrency Miners Targeting GitHub Actions and Azure VMs GitHub Actions and Azure virtual machines (VMs) are being leveraged for cloud-based cryptocurrency mining, indicating sustained attempts on the part of malicious actors to target cloud resources for illicit purposes. "Attackers can abuse the runners or servers provided by GitHub to run an ... | |
 | What It Takes to Tackle Your SaaS Security It's not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc., are amazing for enabling the hybrid workforce and hyper-productivity in businesses today. However, there are three main challenges that have arisen stemming from this evolution: (1) While SaaS apps include a ... | |
| |
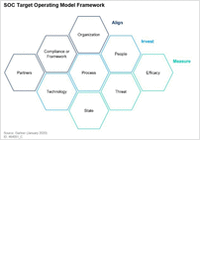 | Create an SOC Target Operating Model to Drive Success Organizations build a security operations center (SOC) to protect against the latest cybersecurity threats. But security leaders responsible for a SOC are often littered with questions about what a SOC does, why it can't be more agile and why breaches still happen after spending so much on security. | |
| |
| This email was sent to myemailku.ghdbrevo2018@blogger.com. You are receiving this newsletter because you opted-in to receive relevant communications from The Hacker News. To manage your email newsletter preferences, please click here.
 Contact The Hacker News: info@thehackernews.com Contact The Hacker News: info@thehackernews.com
Unsubscribe
The Hacker News | Pearls Omaxe, Netaji Subash Place, Pitampura, Delhi 110034 India |
0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home