 |
| |
| |
 | Warning: AI-generated YouTube Video Tutorials Spreading Infostealer Malware Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar. "The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid ... | |
 | Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty security researcher Vera Mens said in a technical write-up. Akuvox E11 ... | |
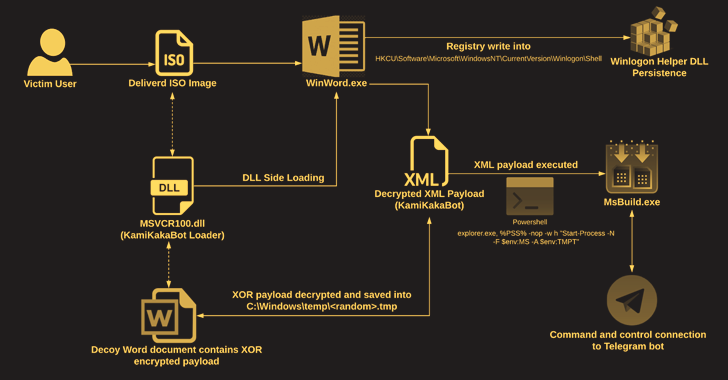 | KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot. Dark Pink, also called Saaiwc, was extensively profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands ... | |
 | BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver secondary payloads like Vidar Stealer and Ursnif. According to cybersecurity company eSentire, the malicious ads are used to spoof a wide range of legitimate apps and services such as Adobe, OpenAPI's ChatGPT, Spotify, Tableau, and Zoom. BATLOADER, as the name suggests, is a loader that's responsible ... | |
 | New Version of Prometei Botnet Infects Over 10,000 Systems Worldwide An updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022. The infections are both geographically indiscriminate and opportunistic, with a majority of the victims reported in Brazil, Indonesia, and Turkey. Prometei, first observed in 2016, is a modular botnet that features a large repertoire of components and several ... | |
 | China-linked Hackers Targeting Unpatched SonicWall SMA Devices with Malware A suspecting China-linked hacking campaign has been observed targeting unpatched SonicWall Secure Mobile Access (SMA) 100 appliances to drop malware and establish long-term persistence. "The malware has functionality to steal user credentials, provide shell access, and persist through firmware upgrades," cybersecurity company Mandiant said in a technical report published this week. ... | |
 | International Law Enforcement Takes Down Infamous NetWire Cross-Platform RAT A coordinated international law enforcement exercise has taken down the online infrastructure associated with a cross-platform remote access trojan (RAT) known as NetWire. Coinciding with the seizure of the sales website www.worldwiredlabs[.]com, a Croatian national who is suspected to be the website's administrator has been arrested. While the suspect's name was not released, ... | |
 | When Partial Protection is Zero Protection: The MFA Blind Spots No One Talks About Multi-factor Authentication (MFA) has long ago become a standard security practice. With a wide consensus on its ability to fend off more than 99% percent of account takeover attacks, it's no wonder why security architects regard it as a must-have in their environments. However, what seems to be less known are the inherent coverage limitations of traditional MFA solutions. While compatible ... | |
| |
| |
| |
| This email was sent to myemailku.ghdbrevo2018@blogger.com. You are receiving this newsletter because you opted-in to receive relevant communications from The Hacker News. To manage your email newsletter preferences, please click here.
 Contact The Hacker News: info@thehackernews.com Contact The Hacker News: info@thehackernews.com
Unsubscribe
The Hacker News | Pearls Omaxe, Netaji Subash Place, Pitampura, Delhi 110034 India |
0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home