 |
| |
| |
 | New Cyber Platform Lab 1 Decodes Dark Web Data to Uncover Hidden Supply Chain Breaches This article has not been generated by ChatGPT. 2022 was the year when inflation hit world economies, except in one corner of the global marketplace – stolen data. Ransomware payments fell by over 40% in 2022 compared to 2021. More organisations chose not to pay ransom demands, according to findings by blockchain firm Chainalysis. Nonetheless, stolen data has value beyond a price tag, and ... | |
 | Researchers Shed Light on CatB Ransomware's Evasion Techniques The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload. CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an "evolution or direct rebrand" of another ransomware strain known as Pandora based on code-level similarities. It's worth noting that the ... | |
| |
 | Emotet Rises Again: Evades Macro Security via OneNote Attachments The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a potent and resilient threat despite attempts by law enforcement to take it down. ... | |
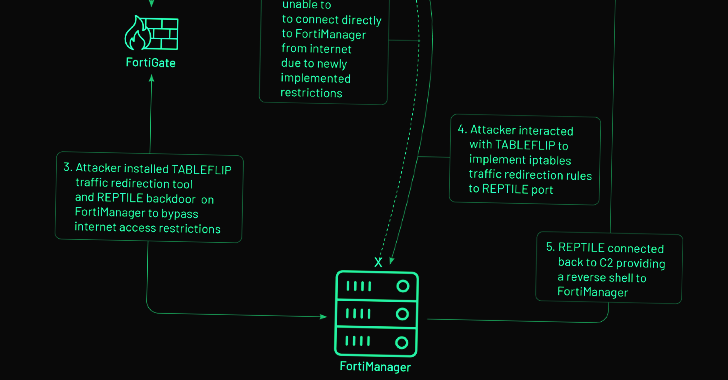 | Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to ... | |
 | Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias "Pompompurin." The development, first reported by Bloomberg Law, comes after News 12 Westchester, earlier this week, said that federal investigators "spent hours inside and outside of a home in Peekskill." "At one point, investigators were ... | |
 | THN Webinar: 3 Research-Backed Ways to Secure Your Identity Perimeter Think of the typical portrayal of a cyberattack. Bad guy pounding furiously on a keyboard, his eyes peeking out from under a dark hoodie. At long last, his efforts pay off and he hits the right combination of keys. "I'm in!" he shouts in triumph. Clearly, there are many problems with this scenario – and it's not just the hoodie. What's even more inaccurate is that most cyber attackers today ... | |
 | LockBit 3.0 Ransomware: Inside the Cyberthreat That's Costing Millions U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware. "The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service (RaaS) model and is a continuation of previous versions of the ransomware, LockBit 2.0, and ... | |
| |
| |
| |
| This email was sent to myemailku.ghdbrevo2018@blogger.com. You are receiving this newsletter because you opted-in to receive relevant communications from The Hacker News. To manage your email newsletter preferences, please click here.
 Contact The Hacker News: info@thehackernews.com Contact The Hacker News: info@thehackernews.com
Unsubscribe
The Hacker News | Pearls Omaxe, Netaji Subash Place, Pitampura, Delhi 110034 India |
0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home